Threats to Power Grid
Yes, many of today’s power grids are very sophisticated and automated. Every single event and piece of equipment is tracked, controlled, measured, and protected. But things aren’t as bright as it seems. As we can see, it turns out that all these advanced toys are easily hackable, meaning that many different areas of the power grid are vulnerable to cyberattacks.

These areas include data storage, automation of distribution, demand management, smart metering infrastructure, and wide area situational awareness.
All it takes is one assault to compromise any number of these subsystems. There are four main types of attacks against power systems that can be distinguished:
- Cyberattacks with the goal of stealing information from servers owned by utilities.
- Cyberattacks that seek to seize control of servers needed for utilities.
- Cyberattacks that attempt to bring down servers that provide utilities.
- Cyberattacks on instruments used for measuring large areas.
Furthermore, we must address the dangers to the smart home segment of the grid, as well as those that come from its interactions with other smart grid components. These encompass eavesdropping, traffic analysis, replay attacks, repudiation, and more threats.
Common cyberattacks targeting infrastructure include:
Denial of Service (DoS) and Distributed Denial of Service (DDoS): Distinct attack vectors designed to undermine the availability of a system’s functionality.
Malicious software: It refers to attacks stemming from the actions of malware, which include viruses, worms, Trojan horses, logic bombs, and similar threats.
Identity spoofing: The unauthorized impersonation of a genuine user or service by methods such as man-in-the-middle attacks, message replay, IP spoofing, or software exploitation.
Password theft: It encompasses prevalent attack methods such as password sniffing, guessing, brute force attacks, dictionary attacks, and social engineering.
Eavesdropping: Unauthorized interception of communication content.
Intrusion: Unauthorized access to cyber assets.
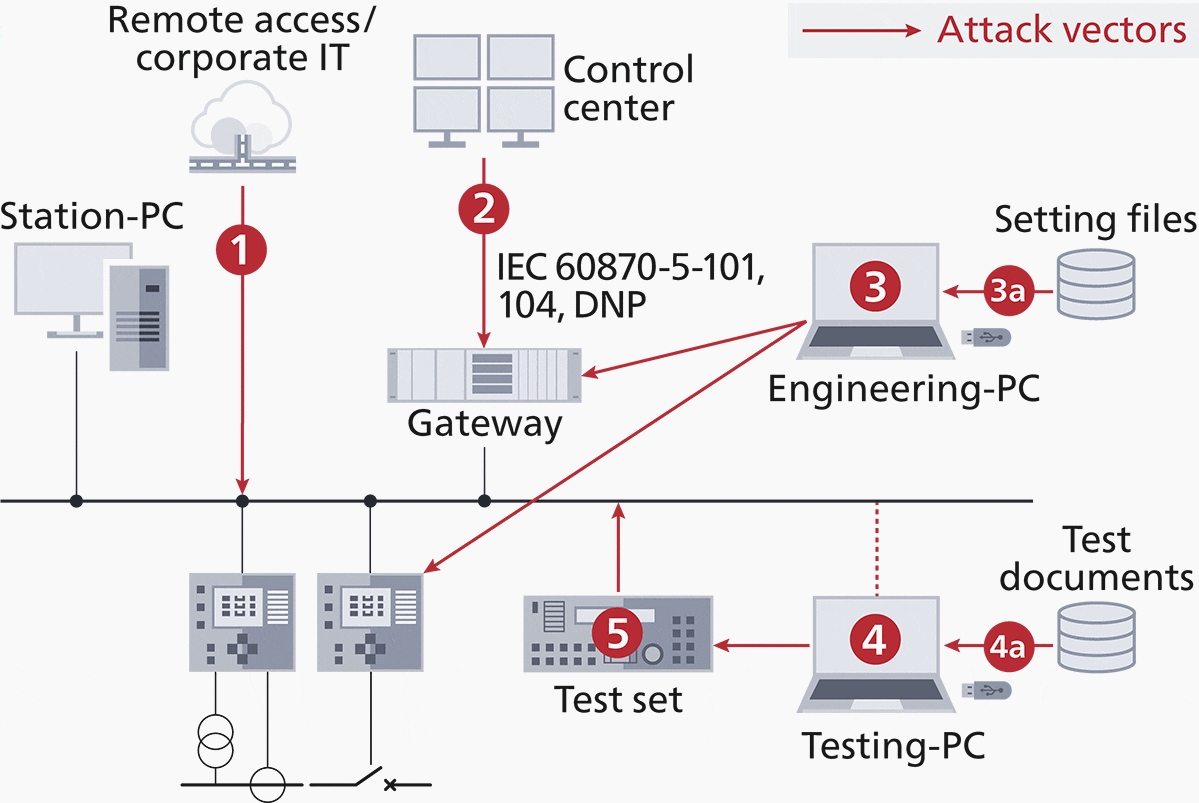
Another access point is via engineering PCs (3) linked to substation equipment or the network.
Figure 1 – Attack vectors of a substation

Side-channel attacks: Assaults that exploit the ancillary characteristics of the targeted system, typically associated with its implementation rather than inherent cybersecurity flaws, encompassing power analysis, electromagnetic analysis, and timing attacks.
The following attacks are included in an alternative list of conventional attacks on the power grid, which is more generic in nature:
- Spoofing,
- Tampering (unauthorised modification of a device or service),
- Repudiation (denying the agency of actions taken in a computer system, information disclosure (obtaining unauthorised access to information),
- Denial of Service,
- Elevation of privilege (illicit gaining of system privileges higher than granted),
- Phishing (extortion of confidential data),
- Cryptanalysis (an extensive set of methods aiming at obtaining a plain text from an encrypted code).
The power sector is currently facing a number of cyberthreats, the most serious of which could be classified as follow:
- Data injection attacks against state estimation,
- DoS and DDoS,
- Targeted Attacks, coordinated attacks, hybrid attacks and Advanced Persistent Threats.
A description of each of these types of attacks is discussed in the following paragraphs.
- Attacks Using Data Injection Against State Estimation
- The Most Used: DoS and DDoS Attacks
- The Most Advanced Cyberattacks (Targeted, Coordinated & Hybrid Attacks, Advanced Persistent Threats)
- Conclusion
- Additional Reading (PDF)
1. Attacks Using Data Injection Against State Estimation
Why state estimation? State estimation is a crucial function in supervisory control and planning of electric power systems. It serves to monitor the state of the grid and allows Energy Management Systems (EMS) for performing important control and planning tasks such as computing optimal power flow, economic dispatch and unit commitment analysis, incorrect data detection or reliability assessments.
The latter include contingency analysis and determination of corrective actions against potential failures in the power system.
Unfortunately, current statistics shows that data injection attacks against state estimation in power distribution systems requires only a little effort, and that attacker can effectively distort the power system.
2. The Most Used: DoS and DDoS Attacks
Attacks that are classified as Distributed Denial of Service (DDoS) are constantly being launched against modern vital infrastructures, including power grids themselves.
Already in 2011, McAfee disclosed that eighty percent of critical infrastructure installations were subjected to a distributed denial of service attack that year, and approximately twenty-five percent are required to cope with DDoS on a weekly basis.










