Continued from How Stuxnet (PLC virus) spreads – Part 1 » Read here
 Stuxnet is a computer worm designed to infect Siemens SIMATIC WinCC and S7 PLC products, either installed as part of a PCS 7 system, or operating on their own. It starts by taking advantage of vulnerabilities in the Windows operating systems and Siemens products. Once it detects a suitable victim, it modifies control logic in specific models of Siemens PLCs. The objective appears to be to sabotage a specific industrial process using two vendors’ variable-frequency drive controllers, along with a supervising safety system for the overall process. While there has been much speculation on Stuxnet’s intended target, recent information suggests it was Iran’s nuclear program and more specifically, its uranium enrichment process.
Stuxnet is a computer worm designed to infect Siemens SIMATIC WinCC and S7 PLC products, either installed as part of a PCS 7 system, or operating on their own. It starts by taking advantage of vulnerabilities in the Windows operating systems and Siemens products. Once it detects a suitable victim, it modifies control logic in specific models of Siemens PLCs. The objective appears to be to sabotage a specific industrial process using two vendors’ variable-frequency drive controllers, along with a supervising safety system for the overall process. While there has been much speculation on Stuxnet’s intended target, recent information suggests it was Iran’s nuclear program and more specifically, its uranium enrichment process.
Stuxnet is capable of infecting both unsupported/legacy and current versions of Windows including Windows 2000, Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008 and Windows 7. It also infects the Siemens STEP 7 project files in such a way that it automatically executes when the STEP 7 project is loaded by an uninfected Siemens system.
How Does Stuxnet Spread?
Stuxnet is considered by many to be one of the most complex and well-engineered worms ever seen. It took advantage of at least four zero-day vulnerabilities and showed considerable sophistication in its exploitation of both the Windows platform and the Siemens systems. Some of the important characteristics of the worm are:
- It propagates slowly between sites, typically via USB flash drives and other “removable” media,
- It propagates quickly within a site via multiple network pathways,
- It searches for many vendors’ anti-virus technologies on machines being attacked and modifies its behavior to avoid detection,
- It contacts a command and control server on the Internet for instructions and updates,
- It establishes a peer-to-peer network to propagate instructions and updates within a site, even to equipment without direct Internet connectivity,
- It modifies PLC programming logic, causing physical processes to malfunction,
- It hides the modified PLC programs from control engineers and system administrators who are trying to understand why their system has malfunctioned,
- It is signed with certificates stolen from one of two major hardware manufacturers, so that no warnings are raised when the worm is installed, and
- If a particular machine is not the intended target, the worm removes itself from the machine after it has replicated itself to other vulnerable media and machines.
The worm propagates using three completely different mechanisms:
- Via infected Removable Drives (such as USB flash drives and external portable hard disks);
- Via Local Area Network communications (such as shared network drives and print spooler services), and
- Via infected Siemens project files (including both WinCC and STEP 7 files).
Within these three, it uses seven different vulnerability exploitation techniques for spreading to new computers in a system. The worm:
- Exploits a zero-day vulnerability in Windows Shell handling of LNK files; a vulnerability present in all versions of Windows since at least Windows NT 4.0,
- Uses several techniques to try to copy itself to accessible network shares and spread from there if at all possible,
- Copies itself to printer servers using a zero-day vulnerability,
- Uses an older “Conficker” RPC vulnerability to propagate through unpatched computers,
- Contacts Siemens WinCC SQLServer database servers and installs itself on those servers via database calls, and
- Puts copies of itself into Siemens STEP 7 project files to auto-execute whenever the files are loaded.
- An earlier version of the worm used a variant of the old “autorun.inf” trick to propagate via USB drives.
In addition to the propagation techniques described above, the worm used two zero-day vulnerabilities to escalate privilege on targeted machines. This provided the worm with “system” access privileges so it could copy itself into system processes on compromised machines.
What Does Stuxnet do to Control Systems?
When first installed on a computer with any STEP 7 software installed, Stuxnet attempts to locate Siemens STEP 7 programming stations and infect these. If it succeeds, it replaces the STEP 7 DLL routines on the programming stations, so that any person viewing a PLC’s logic would not see any changes Stuxnet later makes to the PLC. These actions occur on all computers with STEP 7 software installed, irrespective of whether the compromised computers are connected to PLCs.
Stuxnet then looks for specific models of Siemens PLCs (6ES7-315-2 and 6ES7-417). If it is able to connect to one of these two models, it “fingerprints” the PLC by checking for the existence of certain process configurations and strings in the PLC. If Stuxnet finds what it is looking for in the PLC, it starts one of three sequences to inject different STEP 7 code “payloads” into the PLC. The PLC’s PROFIBUS driver is replaced and the main PLC program block (Organizational Block 1) and the primary watchdog block (Organizational Block 35) are significantly modified. As well, depending on which sequence is selected, between 17 and 32 additional function blocks and data blocks are injected into the PLC.
Two of Stuxnet’s injected payloads are designed to change the output frequencies of specific Variable Frequency Drives (VFDs) and thus the speed of the motors connected to them, essentially sabotaging an industrial process. A third payload appears to be designed to control the overall safety system for the centrifuges.
This payload takes the inputs coming from the PLC’s I/O modules and modifies them so that the PLC safety logic uses incorrect information. The Stuxnet logic then tells the PLC’s outputs to do what it wants. This is possibly to prevent a safety system from alarming on or overriding the changes the worm is making to the VFD operations.
The Target – A High-Security Site
In this part of the analysis, we propose a hypothetical site that is the worm’s target. As noted earlier, we assume this site is following all the guidance provided for “high security” sites in Siemens’ “Security Concept PCS 7 and WinCC – Basic Document.”
It is important to note that the Siemens recommendations for protecting control systems were selected both because the Stuxnet worm specifically targeted Siemens PLCs and because the Siemens recommendations are a good example of existing “best-practice” recommendations.
Networks at a High Security Site
According to the Siemens documentation, the high security site is separated into at least four security zones as illustrated in Figure 4:
- The pink “Enterprise Control Network” zone is the corporate network, which hosts most business users and business accounting and planning systems, such as Enterprise Resource Planning (ERP) systems. The Enterprise Control Network may itself be separated into additional sub-networks, each with their own protections. Such segmentations and protections are typically established and managed by the corporate IT group.
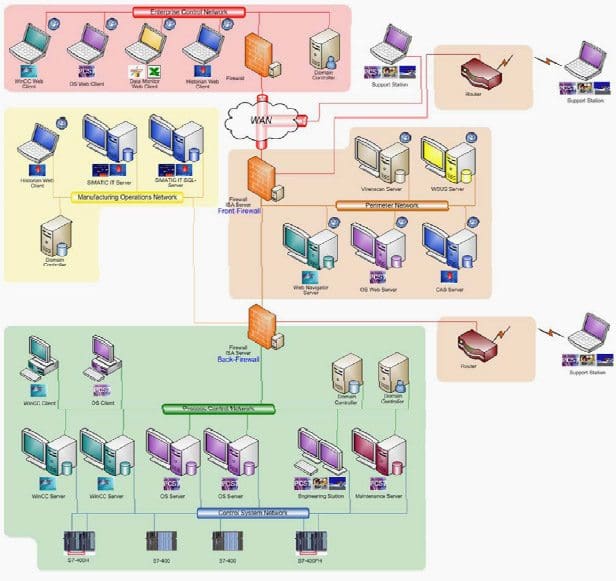
- The yellow “Manufacturing Operations Network” zone hosts the SIMATIC IT servers, which exchange information between the control system, the ERP system, and other important applications on the Enterprise Control Network.
- The brown “Perimeter Network” zone hosts servers that manage equipment in the control system, and servers that provide information to end users on the Enterprise Control Network. This is a common location for servers responsible for providing software patches and updates, including Windows security updates and anti-virus updates. Many of the servers within this zone provide information to end users via web servers and web services. People sometimes refer to this zone as a “demilitarized zone” or DMZ.
- The green security zone hosts two networks: the green “Process Control Network” and the blue “Control System Network.” The Process Control Network hosts the 24×7 plant operators on their Human Machine Interface (HMI) workstations, and is also connected to the WinCC/PCS 7 control system servers. The Control System Network is connected to a number of Programmable Logic Controllers (PLCs) and is also connected to the WinCC/PCS 7 control system servers.
In a large facility, there are frequently multiple “green” zones, one for each control center or operating area. For example, a large chemical plant may have as many as twenty or thirty operating areas, each with their own SIMATIC PCS 7 system, and each controlling a large portion of the facility with both input and output storage facilities to help decouple operational disturbances between areas. These areas are able to operate independently of other portions of the large facility for some period of time. The facility may have many control rooms and corresponding server rooms, each hosting one or more control centers or operating areas.
The corporate wide area network (WAN) connects sites to one another, and connects different kinds of security zones within sites. Corporate IT manages the various enterprise networks and the corporate firewalls which protect enterprise network segments.
Note that while the Process Control Network and the Control System Network are different networks, they are both in the same security zone. WinCC and PCS 7 control system servers have at least two network interfaces, one for each kind of network. The two networks are separated for performance and technological reasons, not security reasons.
In other words, the Control System Network is dedicated to traffic specifically related to “automation” and “control” such as traffic to/from process controllers/PLCs and servers, while traffic on the Process Control Network is utilized for “information” and “display” such as that between HMI’s and servers.
Internet Security and Acceleration (ISA) Servers
In the recommended architecture, Microsoft Internet Security and Acceleration (ISA) Servers protect the plant zones from the WAN. They also protect zones from each other. All traffic between security zones passes through an ISA server. Each ISA server hosts a number of functions, such as firewall services, network address translation, web proxies, virus scanning and secure web server publishing.
All of the ISA servers are configured by default to block connections originating in less-trusted networks, such as the corporate WAN. The ISA servers allow connections, such as web services connections, from clients on less-trusted networks to selected servers, such as web servers, in the Perimeter Network. Servers that receive connections from less-trusted networks are specifically hardened. The ISA servers manage connections to servers in the Perimeter Network, and allow VPN and web connections only for authorized users with legitimate credentials via the WAN.
The ISA servers are also configured to allow machines inside the protected networks to initiate connections “outward” to specific machines and services on less trusted networks. Those connections may pass through the corporate WAN to external servers such as vendor websites on the public Internet. However, connections from protected equipment to arbitrary sites on the Enterprise Control Network or the Internet are not allowed. Just like inbound connections, the outbound connections through the ISA firewalls are “deny by default,” with only specific, approved connections to external servers permitted.
It should be mentioned that Windows ISA Server was originally introduced in 2001 to run on the Windows 2000 platform. It was enhanced over the years with new editions released in 2004 and in 2006, with both releases designed for the Windows Server 2003 platform. The Siemens Security Concept document is based on the ISA Server 2006 platform. Today, Microsoft offers the Forefront Threat Management Gateway which was released in 2009 and builds upon the ISA 2006 platform offering new features including support for the Windows Server 2008 and 2008R2 platforms. For additional information on ISA and Forefront TMG, please consult Microsoft’s product documentation.
Virtual Private Network Connections
The ISA servers also mediate Virtual Private Network (VPN) connections into protected networks. From time to time, workstations and laptops whose security is managed by third parties are allowed to connect to protected networks through the ISA servers. Such connections are labeled as “support stations” in Figure 4. Support stations are used most commonly for remote engineering activities or vendor support activities. The stations may be at the site, or at a remote corporate site, connected indirectly to the corporate WAN, with their access into corporate networks other than the WAN mediated by either corporate firewalls or the ISA servers. The vendors may also be at other “noncorporate” remote sites, connecting directly to the ISA servers from quarantine zones served by routers.
When these support stations access protected network zones through an ISA firewall, the firewall authenticates the VPN connection. If the vendor uses WinCC or other process applications that require access to the Process Control Network, the firewall allows a small number of connections, including WinCC and STEP 7 database connections, to protected servers. For broader access to protected networks, the ISA server allows only VPN connections to remote access servers running Microsoft Terminal Services or Remote Desktop Services. These are sometimes referred to as “jump hosts”, and are intended to provide isolation between the untrusted hosts, such as support laptops, and the trusted hosts such as the servers and workstations on protected networks.
Host Hardening and Malware Prevention
In addition to the firewall and perimeter protections the ISA servers provide, a variety of host hardening and malware prevention mechanisms are also in place, as specified by the Siemens security architecture. On the Enterprise Control Network, all hosts are part of a comprehensive patch management program that provides automated and managed installation of critical software patches and hot fixes. All hosts have anti-virus and anti-spyware products installed, and signatures for these products are distributed to all hosts immediately upon receipt from the anti-malware vendors.
Hosts have only those applications installed and services enabled that are essential to business functions. Enterprise workstations have access to the open Internet, but all web, ftp and email traffic into the Enterprise Control Network is scanned for spam and malware at the Enterprise Control Network firewall. Select workstations on the Enterprise Control Network have VPN access configured to hosts on the Manufacturing Operations Network and hosts on the Perimeter Network, but no workstations on the Enterprise Control Network have VPN access directly into the Process Control or Control System Networks.
On the Manufacturing Operations Network and the Perimeter Network all hosts are part of the security program implemented at the corporate level. All hosts are current with Siemens patches, Microsoft operating system and application patches, third party application patches, anti-virus and anti-spyware signatures, and all hosts have been reviewed to ensure that only applications and services needed for the correct operation of the host and appropriate network are running. On the Process Control Network and Control System Network, hosts are hardened and are running antivirus software, but the hosts are not part of the corporate patch management system. Operations manages patches on these critical networks, and subjects new Siemens, Microsoft and third-party patches to a rigorous testing process before approving the patches for deployment on critical system components.
The Microsoft Windows Server Update Services (WSUS) servers manage deployment of approved patches, and such deployment is staged so that if unexpected problems arise when patches are deployed, the affected equipment can be taken offline and rolled back without impacting the overall performance of the control system. In addition, operations manages the anti-virus servers for
Process Control and Control System Networks, testing all new signature sets before approving them for deployment, and staging deployment of signature sets just like patch deployment is staged. The WSUS servers also provide management of the deployment of patches allowing users to configure the specific hosts and their timing and sequencing of installation in order to minimize any risk associated with patch rollout. This ensures that equipment that develops unexpected problems because of new patches and signature sets can be taken offline and repaired without affecting the overall performance of the control system.
To be continued soon! Subscribe and be informed – HERE



